Ethanalyzer is a NX-OS protocol analyzer tool based on Wireshark. Wireshark is an open source analyzer that decodes packets captured by libpcap (Capture Library). Cisco NX−OS runs on top of the Linux kernel, which uses the libpcap library to support packet capture. The Ethanalzyer is a command-line version of Wireshark that captures and decodes packets, and can be used to troubleshoot the network and analyze control-plane traffic. The Ethanalyzer uses the same capture file syntax as tcpdump. More information on tcpdump can be found at http://www.tcpdump.org/tcpdump_man.html
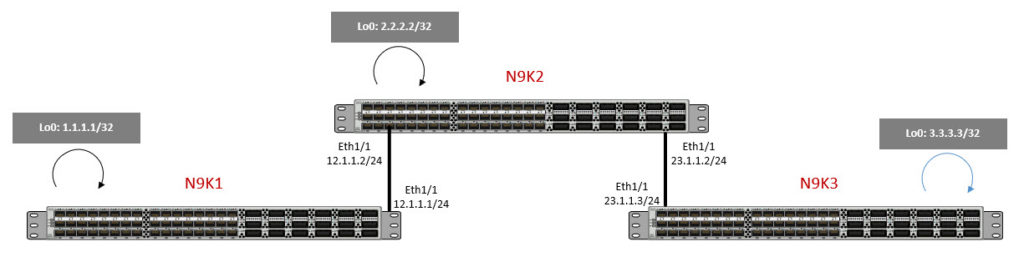
Think of it as Wireshark baked into NX-OS. No external sniffer is needed here and we can capture packets Rx/Tx CPU. We can also use Ethanalyzer with ACLs to capture data-plane packets. This is the topology we will be working with today.
Here, we have daisy-chained three N9Ks and each N9K has a loopback address per the diagram above.
Ethanalyzer is defined in 3 steps:
- Step 1. Define capture interface.
- Step 2. Define Filters: Set the capture filter or display filter.
- Step 3. Define the stop criteria.
We have basically two kinds of filters that can be used here: capture filter & display filter
- Capture filter: Only frames that matches the filer are captured
- Display filter: Display packets matching filters from the captured set of packets
Note that by default, Ethanalyzer captures only up to 10 frames. This value can be increased by setting the limit-captured-frames option where 0 = No limit.
To start a capture, all we’d need is the following command:
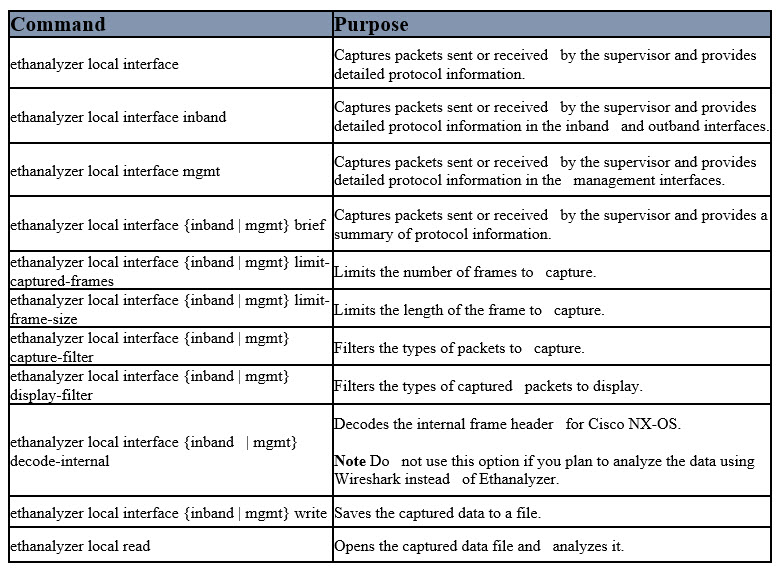
ethanalyzer local interface[inband | mgmt] options, with the following options:
- Autostop: Capture autostop condition
- capture-filter: Filter on Ethanalyzer capture
- capture-ring-buffer: Capture ring buffer option
- decode-internal: Include internal system header decoding
- detail: Display detailed protocol information
- display-filter: Display filter on frames captured
- limit-captured-frames: Indicates the maximum number of frames to be captured
- limit-frame-size: Capture only a subset of a frame
- write: Identifies the filename to save capture to
See below specific commands:
Let’s now dive into the CLI.

 Hi, I'm Pape ! Folks call me Pop. I'm CCIE #48357. I love what I do and enjoy making tech easier to understand. I also love writing, so I’m sharing my blog with you
Hi, I'm Pape ! Folks call me Pop. I'm CCIE #48357. I love what I do and enjoy making tech easier to understand. I also love writing, so I’m sharing my blog with you
Leave a Reply