bash-4.2# tcpdump -r routeleak.pcap
reading from file routeleak.pcap, link-type EN10MB (Ethernet)
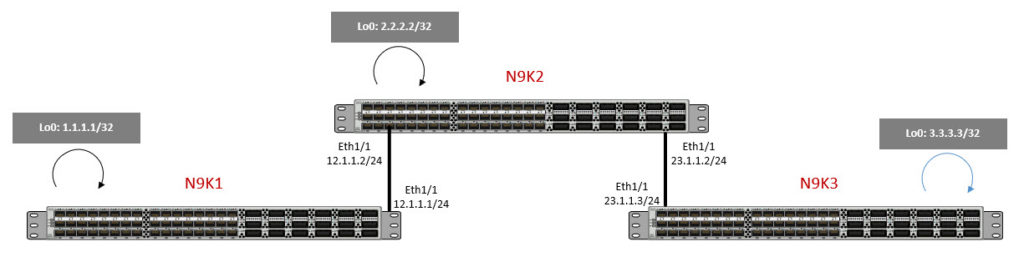
03:18:14.030612 IP 23.1.1.3 > 224.0.0.10: EIGRP Hello, length: 40
03:18:14.636635 IP 23.1.1.3.60196 > 12.1.1.1.ssh: Flags [S], seq 1294388881, win 16384, options [mss 536,nop,wscale 0,nop,nop,TS val 315198 ecr 0], length 0
03:18:14.640347 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [S.], seq 2455402593, ack 1294388882, win 16768, options [mss 536,nop,nop,TS val 313075 ecr 315198], length 0
03:18:14.642699 IP 23.1.1.3.60196 > 12.1.1.1.ssh: Flags [.], ack 1, win 16768, options [nop,nop,TS val 315199 ecr 313075], length 0
03:18:14.643994 IP 23.1.1.3.60196 > 12.1.1.1.ssh: Flags [P.], seq 1:27, ack 1, win 16768, options [nop,nop,TS val 315199 ecr 313075], length 26
03:18:14.689275 IP 23.1.1.2 > 224.0.0.10: EIGRP Hello, length: 40
03:18:14.714286 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [P.], seq 1:32, ack 27, win 16742, options [nop,nop,TS val 313076 ecr 315199], length 31
03:18:14.718448 IP 23.1.1.3.60196 > 12.1.1.1.ssh: Flags [.], seq 27:551, ack 32, win 16768, options [nop,nop,TS val 315199 ecr 313076], length 524
03:18:14.718624 IP 23.1.1.3.60196 > 12.1.1.1.ssh: Flags [P.], seq 551:931, ack 32, win 16768, options [nop,nop,TS val 315199 ecr 313076], length 380
03:18:14.722292 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [P.], seq 32:424, ack 551, win 16244, options [nop,nop,TS val 313076 ecr 315199], length 392
03:18:14.827989 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [.], ack 931, win 16768, options [nop,nop,TS val 313077 ecr 315199], length 0
03:18:14.830501 IP 23.1.1.3.60196 > 12.1.1.1.ssh: Flags [P.], seq 931:1011, ack 424, win 16768, options [nop,nop,TS val 315200 ecr 313076], length 80
03:18:14.842121 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [P.], seq 424:824, ack 1011, win 16768, options [nop,nop,TS val 313077 ecr 315200], length 400
03:18:14.851933 IP 23.1.1.3.60196 > 12.1.1.1.ssh: Flags [P.], seq 1011:1027, ack 824, win 16768, options [nop,nop,TS val 315201 ecr 313077], length 16
03:18:14.962113 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [.], ack 1027, win 16768, options [nop,nop,TS val 313078 ecr 315201], length 0
03:18:14.964916 IP 23.1.1.3.60196 > 12.1.1.1.ssh: Flags [P.], seq 1027:1079, ack 824, win 16768, options [nop,nop,TS val 315202 ecr 313078], length 52
03:18:14.977827 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [P.], seq 824:876, ack 1079, win 16768, options [nop,nop,TS val 313078 ecr 315202], length 52
03:18:14.979986 IP 23.1.1.3.60196 > 12.1.1.1.ssh: Flags [P.], seq 1079:1147, ack 876, win 16768, options [nop,nop,TS val 315202 ecr 313078], length 68
03:18:14.991010 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [P.], seq 876:1028, ack 1147, win 16768, options [nop,nop,TS val 313078 ecr 315202], length 152
03:18:14.995734 IP 23.1.1.3.60196 > 12.1.1.1.ssh: Flags [P.], seq 1147:1247, ack 1028, win 16768, options [nop,nop,TS val 315202 ecr 313078], length 100
03:18:15.001740 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [P.], seq 1028:1096, ack 1247, win 16768, options [nop,nop,TS val 313078 ecr 315202], length 68
03:18:15.134580 IP 23.1.1.3.60196 > 12.1.1.1.ssh: Flags [.], ack 1096, win 16768, options [nop,nop,TS val 315203 ecr 313078], length 0
03:18:18.206618 IP 23.1.1.3.60196 > 12.1.1.1.ssh: Flags [P.], seq 1247:1331, ack 1096, win 16768, options [nop,nop,TS val 315233 ecr 313078], length 84
03:18:18.227503 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [P.], seq 1096:1148, ack 1331, win 16768, options [nop,nop,TS val 313110 ecr 315233], length 52
03:18:18.235354 IP 23.1.1.3.60196 > 12.1.1.1.ssh: Flags [P.], seq 1331:1415, ack 1148, win 16768, options [nop,nop,TS val 315233 ecr 313110], length 84
03:18:18.240117 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [P.], seq 1148:1184, ack 1415, win 16768, options [nop,nop,TS val 313110 ecr 315233], length 36
03:18:18.243018 IP 23.1.1.3.60196 > 12.1.1.1.ssh: Flags [P.], seq 1415:1551, ack 1184, win 16768, options [nop,nop,TS val 315234 ecr 313110], length 136
03:18:18.246982 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [P.], seq 1184:1236, ack 1551, win 16768, options [nop,nop,TS val 313110 ecr 315234], length 52
03:18:18.250965 IP 23.1.1.3.60196 > 12.1.1.1.ssh: Flags [P.], seq 1551:1943, ack 1236, win 16768, options [nop,nop,TS val 315234 ecr 313110], length 392
03:18:18.256604 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [P.], seq 1236:1360, ack 1943, win 16768, options [nop,nop,TS val 313110 ecr 315234], length 124
03:18:18.259358 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [P.], seq 1360:1412, ack 1943, win 16768, options [nop,nop,TS val 313110 ecr 315234], length 52
03:18:18.368109 IP 23.1.1.3.60196 > 12.1.1.1.ssh: Flags [.], ack 1412, win 16768, options [nop,nop,TS val 315235 ecr 313110], length 0
03:18:18.504320 IP 23.1.1.3 > 224.0.0.10: EIGRP Hello, length: 40
03:18:18.741992 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [.], seq 1412:1936, ack 1943, win 16768, options [nop,nop,TS val 313115 ecr 315235], length 524
03:18:18.746902 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [.], seq 1936:2460, ack 1943, win 16768, options [nop,nop,TS val 313115 ecr 315235], length 524
03:18:18.749880 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [P.], seq 2460:2504, ack 1943, win 16768, options [nop,nop,TS val 313115 ecr 315235], length 44
03:18:18.761270 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [P.], seq 2504:2556, ack 1943, win 16768, options [nop,nop,TS val 313115 ecr 315235], length 52
03:18:18.761534 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [P.], seq 2556:2640, ack 1943, win 16768, options [nop,nop,TS val 313115 ecr 315235], length 84
03:18:18.762135 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [P.], seq 2640:2724, ack 1943, win 16768, options [nop,nop,TS val 313115 ecr 315235], length 84
03:18:18.762984 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [P.], seq 2724:2840, ack 1943, win 16768, options [nop,nop,TS val 313115 ecr 315235], length 116
03:18:18.763801 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [P.], seq 2840:2956, ack 1943, win 16768, options [nop,nop,TS val 313115 ecr 315235], length 116
03:18:18.764702 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [P.], seq 2956:3072, ack 1943, win 16768, options [nop,nop,TS val 313115 ecr 315235], length 116
03:18:18.765546 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [P.], seq 3072:3188, ack 1943, win 16768, options [nop,nop,TS val 313115 ecr 315235], length 116
03:18:18.766424 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [P.], seq 3188:3304, ack 1943, win 16768, options [nop,nop,TS val 313115 ecr 315235], length 116
03:18:18.767292 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [P.], seq 3304:3420, ack 1943, win 16768, options [nop,nop,TS val 313115 ecr 315235], length 116
03:18:18.768096 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [P.], seq 3420:3536, ack 1943, win 16768, options [nop,nop,TS val 313115 ecr 315235], length 116
03:18:18.768770 IP 23.1.1.3.60196 > 12.1.1.1.ssh: Flags [.], ack 2460, win 16768, options [nop,nop,TS val 315238 ecr 313115], length 0
03:18:18.808496 IP 23.1.1.3.60196 > 12.1.1.1.ssh: Flags [.], ack 3536, win 16768, options [nop,nop,TS val 315239 ecr 313115], length 0
03:18:18.916995 IP 12.1.1.1.ssh > 23.1.1.3.60196: Flags [P.], seq 3536:3588, ack 1943, win 16768, options [nop,nop,TS val 313116 ecr 315239], length 52
03:18:19.025147 IP 23.1.1.3.60196 > 12.1.1.1.ssh: Flags [.], ack 3588, win 16768, options [nop,nop,TS val 315241 ecr 313116], length 0
03:18:19.427295 IP 23.1.1.2 > 224.0.0.10: EIGRP Hello, length: 40
bash-4.2#

 Hi, I'm Pape ! Folks call me Pop. I'm CCIE #48357. I love what I do and enjoy making tech easier to understand. I also love writing, so I’m sharing my blog with you
Hi, I'm Pape ! Folks call me Pop. I'm CCIE #48357. I love what I do and enjoy making tech easier to understand. I also love writing, so I’m sharing my blog with you
Thank you for your good information!!!
I understand how to use tcpdump on Nexus9k platform.
Cisco’s website is complicated , so it is hard to access information I need.
I was able to solve a problem by using tcpdump!
Thanks!!!
I’m glad this has been useful !
You made life easy mate!!!
Thank you very much for your effort…
Good Job!