Packet-tracer is a built in utility on the Nexus 9000 that’s used to trace the path of a packet transiting the switch. This is extremely useful in terms of troubleshooting as this tool can confirm whether or not a specific traffic flow is traversing the switch. It’s also useful to pinpoint packet loss as it displays counters to track flow statistics. Note that this can’t be used for ARP traffic, IPv6 and non-IP based flow at the time of this post.
We will be working with the following setup today.
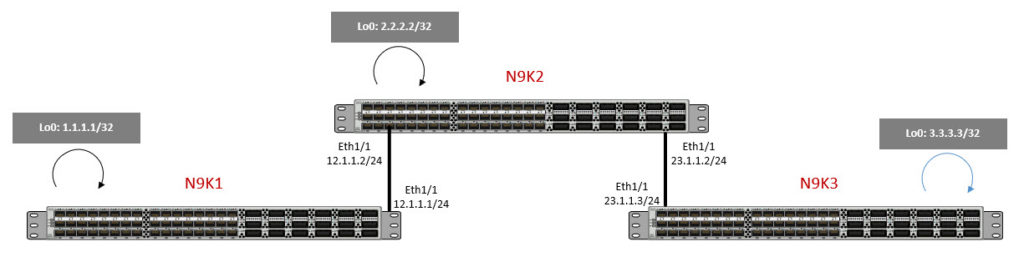
Here, we have daisy-chained three N9Ks and each N9K has a loopback address per the diagram above.
Packet-tracer commands are EXEC level commands.
N9K-9508#test packet-tracer src_ip <src_ip> dst_ip <dst_ip> <==== provide your src and dst ip N9K-9508#test packet-tracer start <==== Start packet tracer N9K-9508#test packet-tracer stop <==== Start packet tracer N9K-9508#test packet-tracer show <==== Check for packet matches Let's dive into the CLI. Here we're going to SSH to N9K1 from N9K3 and run our trace. Let's first configure packet tracer on N9K2.

 Hi, I'm Pape ! Folks call me Pop. I'm CCIE #48357. I love what I do and enjoy making tech easier to understand. I also love writing, so I’m sharing my blog with you
Hi, I'm Pape ! Folks call me Pop. I'm CCIE #48357. I love what I do and enjoy making tech easier to understand. I also love writing, so I’m sharing my blog with you
Leave a Reply